Cloud migration, microservices and container adoption are driving application modernization.
Migrating to the cloud doesn't have to be complicated.
Application vulnerabilities are often uncovered late because DevOps and security processes can be disjointed. Application security services professionals with a deep understanding of the software development lifecycle (SDLC) can help assess and transform your “shift-left” and DevSecOps practices. Application security services are focused around three key areas of DevSecops, training and threat modeling. DevSecOps services help development, security and operations teams share skills for greater collaboration.
Application Security Consulting Services
There are a wide array of Application Security tools, each with its own specific use case and function. Some of the most common include:
Application Security Testing Services
Ensure Business as Usual (BaU) and maintain a standard customer experience during migration. Our extensive experience in successfully migrating mission critical workloads means that activities are on time, within budget, and with minimal business disruptions.
Application Security Consulting
Avail customized migration services with our certified cloud practitioners who have years of migration experience for complex and challenging projects. This warrants adherence to industry best practices such as deploying governance frameworks, network optimization, adoption of automation, and implementing monitoring benchmarks.
Threat Modeling Services
Integrate DevOps within your cloud migration journey by leveraging our DevOps thinking. Our DevOps best practices set up a streamlined operations ecosystem, backed by IaC, automation tools, and CI/CD pipelines to help you extract the best out of cloud initiatives.
DevSecOps Consulting
Reach goals faster with battle-tested frameworks and boilerplates. This ensures that the setupa is quick and there are negligible operational overheads. Certified cloud engineers increase development throughput, avoiding long learning curves to accelerate the migration journey.
Security Code Review
Avail personalized training and adoption plans for the cloud, consisting of runbooks, templates, and FAQs for managing the change caused by cloud adoption. Cuelogic also runs specialized, user-focused workshops/training to increase awareness around operations and maintenance know-how.
Security and Testing Methods
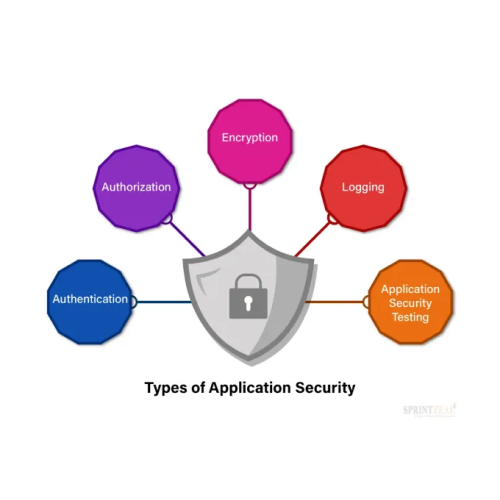
Encrypting sensitive data that flows between end-users and the cloud in cloud-based applications, Verifying user identities, Authorization, Encryption, logging, Application Security Testing and tools like Design review, white-box or code review, black-box security audits, automated tooling, coordinated vulnerability platforms
Application Security execution details
No software code is unbreakable, but there are ways to reduce applications vulnerability.
Applicability Landscape
Web applications, Software as a Service, API web services, Mobile apps, IoT devices, Desktop applications
What to expect
Meet compliance requirements on vulnerability management, Find and fix application security bugs in your software code, Lower the risks of data breaches, service disruptions, and bad publicity, Test the efficiency of Secure Software Development Lifecycle, Measure the effectiveness of your application security investment.
Outcomes of all the efforts
Immediate reports of all Critical application security bugs. A high-level Executive Summary for top management and clients, A non-confidential Attestation Letter to demonstrate your application security effort, The report with all findings and clear recommendations on fixing them, The evidence, descriptions, and steps to reproduce for all findings, You are eligible for a free retest of all findings once you fix them,
Get a 30-minute, no-cost strategy session with a Cloud Services expert